As web applications today are using http to do the communication between the client and server, the security for the communication become more and more important. Https is a scheme that a new SSL layer is added between the http and TCP/IP. The SSL is used to secure the communication based on http. As http and https are widely used today, some developer like me who do not well understand how https works has struggled alot when doing web developement. Therefore, I would like to share some of my understanding of how https works.
Https is originally developed by Netscape. Https 1.0 and http2.0 are found containing some bugs therefore they are not widely used. Https uses a combination of cipher algorithms for example asymmetric cipher. Best way to understand how https works is using pictures:
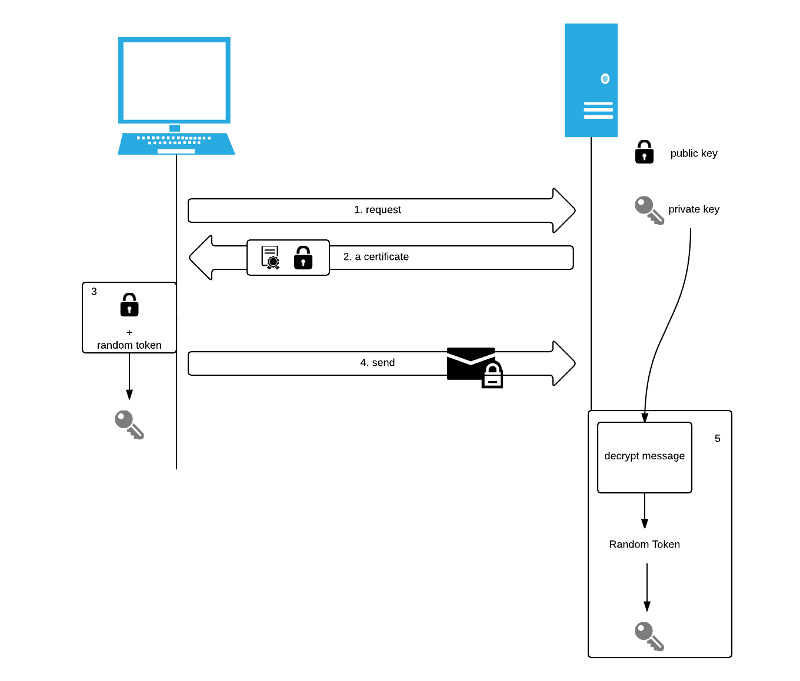
- A client start a request to the server.
- The server received the request from the client and send a certificate as respones. In the certificate, a public key is included (asymmetic cipher algorithm is used). The public key can be viewd as a locker send by the server which is used by the client to encrypt message. Meanwhile, server has a private key to decrypt the ciphertext.
- The client has received the certificate. Then client will firstly verify the certificate. If the certificate is varified, the client will extract the public key from the certificate. A random token is generated. This random token is going to be used to generate new keys for the use of encrypting and decrypting the message between server and client. In some article or book, this random token is called pre-master secrete.
- Now the client will encrypt this random key by the public key received from the server and then send back to server.
- The server received the encrypted message which contains a random token. The server will decrypt the message to get the random token. Then new keys is generated by the random token.
From now on, a secure connection is setup between the client and server.